
Phishing is a cybercrime which makes use of social engineering techniques in order to steal user data like login credentials and financial details. The most common type of phishing attacks take place through emails. An attacker sends an email pretending to be from a trusted source tricking the victim into opening the email and clicking on the attached link (or download attachments).
Once the malicious link is clicked, one or more of these things will happen:
- Redirects to a fake website which requests personal information (login credentials, credit card details etc)
- Installs malware on your system
- Leads to a ransomware attack by freezing your device
- Revealing of sensitive information
- Installation of software with the intent of stealing information (Keyloggers)
An individual victim of a phishing scam may face dire consequences like unauthorized purchases, identity theft and stolen funds. However when phishing changes to long term attacks like an APT (Advanced persistent Threat) the consequences are much more severe. These type of attacks are targeted mostly on organizations or businesses where the attackers infiltrate the networks and stay in the background collecting as much information as possible. An organization which falls under this type of attack usually faces high financial losses, loss of reputation and consumer trust.
Types of phishing
1. Email Phishing
This is one of the most common and the easiest types of phishing techniques to get data from users without them knowing. These attacks can happen when an email is sent through a familiar name or by sending an email impersonating your superiors or by impersonating an organization. Just by seeing the name of the email and the urgency of the mail, users tend to click on the link.
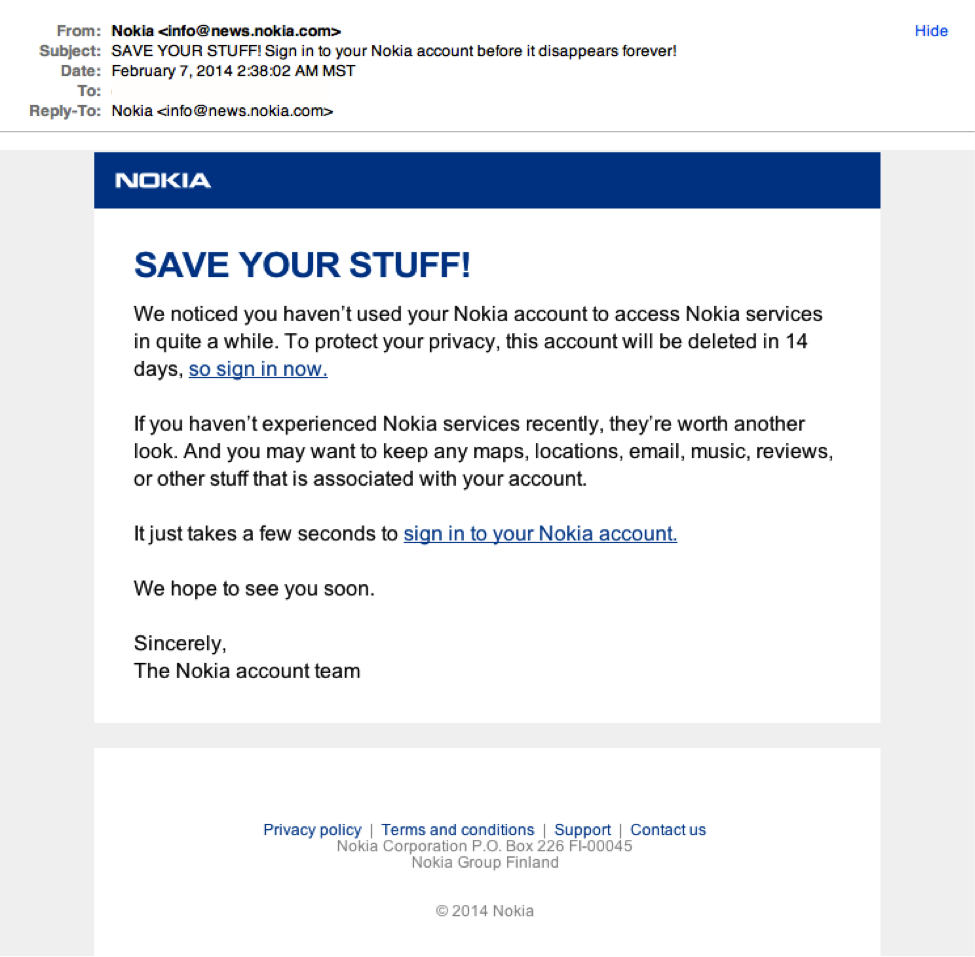
2. URL Phishing
The attack is based on sending the phishing pages URL to the victims directly. This has a higher chance of getting opened because people are prone to click on links out of sheer curiosity, always ready to accept friend requests and messages. The attackers will send the link in numerous ways in order to trick the victim on clicking the link.
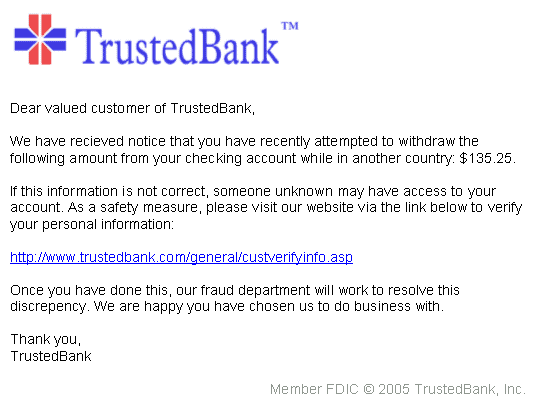
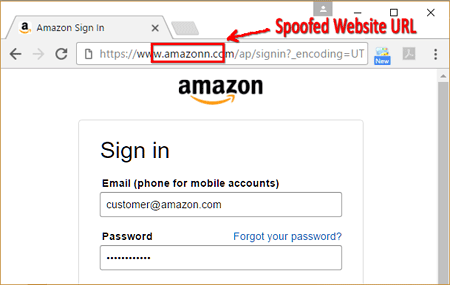
3. Website spoofing
Website spoofing is similar to email spoofing however a lot more work has to be done into pulling this off. This is done by copying the design, content and the user interface of a legitimate website and having a very similar URL. Once the victim is on the site, they will provide there data directly to the attackers.
4. Man in the middle attack
A man in the middle attack takes place between 3 entities where two are legitimate entities and the third party eavesdropping on them. The MiTM will have the possibility to see the conversations and collect sensitive information from both parties.
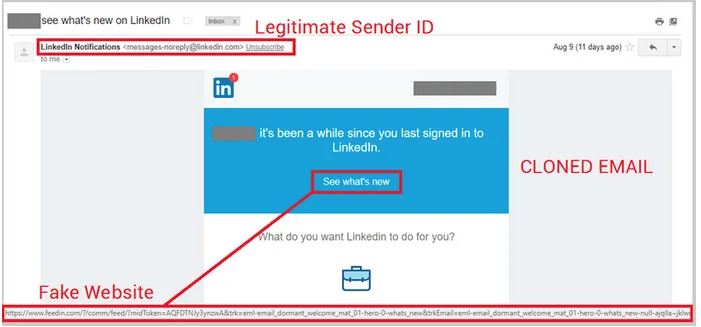
5. Clone phishing
In a clone-phishing attack the hackers make an almost identical copy of a previously received email containing any link or attachment. The link/attachment is replaced with the malicious link or attachment. This email is forwarded to the contacts of the victim’s inbox. This is really dangerous because the victim will never suspect that the email is fake.
6. Malware injection
This happens when malware is injected to a victim through emails. It’s a very common type of phishing attack. The usual objectives of a malware attack is to: Hijack a user’s computer, Stealing sensitive information, conducting illegal activities or to launch a DDoS attack.
How to recognize phishing
Sense of Urgency
This is one of the tactics used by “Phishers” where they ask user’s to act fast in order to get the limited time offer. Sometimes they request users to update their account details in a limited time or else it will be suspended. If you receive these kind of emails, just ignore them. All reliable businesses will give ample amount of time before terminating their accounts.
However if you’re in doubt, go to the official website and check it for yourself without clicking on any links in the email.
Too good to be true
Lucrative offers, attention grabbing statements and visually pleasing information are intended to draw in victims. Many emails, notifications and pop-ups appear where it shows that you have won an iPhone, a lottery or a lavish prize. Don’t click on these links because if it seems too good to be true it probably is!!
Hyperlinks
When you see a hyperlink, it might not always be what it seems. Hovering over the links on websites and emails will show you exactly what the URL is. It might say something else whereas once you click you will end up in a completely different place. As the saying goes, ‘don’t judge a book by the cover’ works in the digital world too.
Unusual sender
If you get emails or messages from an unusual sender avoid it completely. If it’s from someone that you know but still the context and the message seems sketchy, then the best way is to avoid it. If the content and the message is suspicious avoid it completely.
Attachments
If there are attachments in your email which you didn’t expect or doesn’t make sense, do-not open it. These attachments might contain malware which includes viruses, ransomware and spyware.
How to protect yourself from phishing attacks
Most of the phishing scams happen through emails and while your spam filter keeps the phishing emails out of your inbox, the cyber criminals will always find a way to end up in your inbox. Here are some tips to avoid being a victim of a phishing scam.
- Use a security software and always keep it up-to date. Keep your Operating System up-to date and all other software on your device. These updates usually come equipped with security patches which were found recently.
- Set automatic updates to all your mobile applications
- Use two factor authentication for all your accounts (if possible). Some accounts have an extra security feature where you will need to provide two or more credentials in order to gain access to your account.
- Backup your data. Always have a backup of all your most important data on an external hard drive or in a cloud storage.
- Once you’re on a website always check if it is equipped with an SSP certification. Google recommends that it’s much safer to visit and share information with a site equipped with an SSL.
On a final note
There’s a lot of threats out there in the cyberspace. When it comes to phishing scams you should pay close attention to the details. First phishing scam was in 2004 and the technology and people have changed drastically since then. These types of attacks are based on social engineering which tricks the user to provide sensitive information willingly. You can follow the tips and tricks mentioned here but the cyber criminals will always find a way because nothing is 100% safe on the internet. The best protection against phishing scams and most of the threats on the internet is to use common sense and avoid them from the initial signs.
Do you value your privacy online?
Use VPN Surf and surf safely and securely in the open waters of the internet.
