
If you’re here probably it’s due to curiosity or heard it in an office conversation or this was the random place in the internet you ended up. Well since you’re here let’s go ahead and know what a ransomware is, how you get it, a little history (not going to be boring), who it targets and what you should do to protect against it.
So what is a Ransomware?
A ransomware or ransom malware is a malicious software which locks and encrypts a victim’s device data and demands a ransom to be paid in order to restore access. In most cases the cybercriminals set a time limit for the ransom to be paid before losing the data forever. However there is no guarantee of retrieving access to your device even after the payment is made.
Once you are under a ransomware attack, all your personal files, documents, photos, financial information will be encrypted and you won’t be able to open them. If the attackers will not provide the decryption key, then most likely you won’t be able to get access to your data or device.
Let’s tap into the beginnings
Initially ransomware started off by targeting individuals but this changed soon afterwards. The attacks started to target larger groups like businesses with the intent of getting a higher profit. The following is a list of ransomware attacks from the beginning to where it is now.
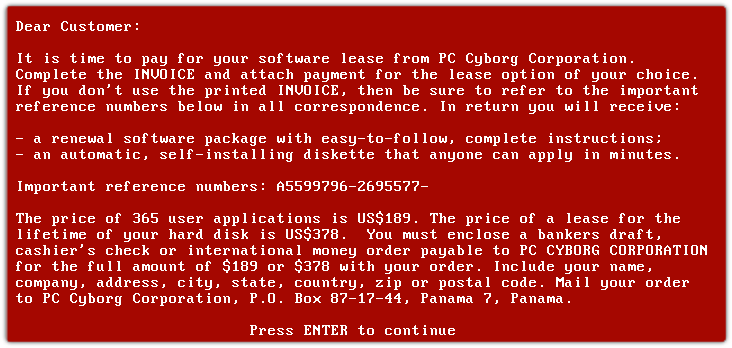
- AIDS Trojan, late 1980s: Aids Info Disk or PC Cyborg Trojan which was the first ransomware released by AIDS researcher Joseph Popp. This counts the number of time the computer has been booted and once it reaches 90, the whole C: drive would be encrypted. Unless the ransom was paid to the PC Cyborg Corporation the computer will be inaccessible.
- PGPCode, 2004: Once this was installed on a computer it would encrypt files with specific extensions like .doc, .html, .xls and much more. Unless a ransom is paid the files will remain inaccessible.

- WinLock, 2007: This ransomware didn’t encrypt user files but locked the victim’s from their desktops and displayed pornographic images on their screen. In order to remove the images, the victims had to pay a ransom via a paid SMS message.
- Reveton, 2012: Once a victim was infected, the user will be locked from their device and a message will be shown on the desktop which appears to come from law enforcement agencies like the FBI. It states that the victim is accused of committing false crimes and had to pay a fine to gain access to their devices.

- CryptoLocker, 2013: This malware encrypted certain files on the victims computer and displayed a message demanding a ransom to be paid within a given time limit. The ransom was supposed to be paid using bitcoin and pre-paid cash vouchers. However there was no guarantee if the files will be decrypted. These attackers gained about $3 million before being taken down.

- Locky, 2016: This malware is delivered by email looking like an invoice which needs to be paid with a Microsoft Word attached which contains malicious macros. Once the document is opened it appears to be jumbled text and symbols while having the phrase “Enable Macro if data encoding is incorrect” which is a social engineering technique. Once accepted the ransomware encrypts the files and instructs them on paying the ransom.

- WannaCry, 2017: This ransomware targets computers running Microsoft Windows operating system and encrypts the data and demand the ransom to be paid using bitcoins.

As you can see that the ransomware has progressed from the beginning and it’s continuously evolving and becoming a very popular means of cyber-attack.
Now let’s break down the types of Ransomware out there
Lockers: These type of ransomware are known for infecting your operating system resulting in being completely locked out of your devices and computers.
RaaS: Ransomware as a Service or Raas is a type of malware introduced by a hacker or group of hackers. They handle everything from distributing the ransomware, managing the decryption keys (software that restores data access). In simple terms, you can buy the ransomware and the decryption keys from these cybercriminals.
Crypto Malware: This type of malware can cause a lot of damage as it encrypts your files, folders and hard-drives. This was the type of malware that was used in the WannaCry ransomware attack.
Doxware: This is commonly known as leakware which threatens the victims of publishing their stolen data if a ransom is not paid. Since majority of people store sensitive information in their personal computers, their prone to pay for the ransom.
Mac ransomware: Mac operating systems were affected by their first ransomware in 2016 known as KeRanger. This infected Apple users through an app called Transmission which encrypted the victim’s files.
So what should you do to prevent a ransomware attack?
Ransomware is a very profitable market for the cybercriminals out there and it’s pretty difficult to stop. So as doctors say, “prevention is better than cure”.
- Use a security software: Install and use a trusted security software which offers more services than just antivirus features
- Keep your antivirus up-to date: New threats emerge frequently so it’s better to have the security software up-to-date equipped to protect you.
- Use cloud services: This will help reduce the ransomware infection as you can restore your files back if an infection comes into play.
- Update your operating System and other software: These constant updates include new features plus patches for newly discovered security vulnerabilities that could be used by cybercriminals.
- Don’t open email attachments automatically: The most common way of transmitting ransomware and malware is through emails and attachments. If it doesn’t seem like a familiar email, delete it.
- Back up important data: Backup you’re most important files because if you fall under a ransomware attack you won’t have to pay a ransom and your data can be restored once the malware is removed.
- DO NOT PAY THE RANSOM: There’s no guarantee if you will get your data back. Avoid paying the ransom and this is also recommended by the FBI.
Stay safe online!
Do you value your privacy online?
Use VPN Surf and surf safely and securely in the open waters of the internet.
