
The first thing that lights up your mind when you hear “spam” could be one of two things. Either the delicious canned meat or the unwanted annoying emails you find on your email. Well, this article is all about the unwanted emails: spam.
Have you ever come across the following types of emails?
- Buy this pill to grow your hair!
- Get this cream to remove all the problems from your skin!
- Congratulations, you won a huge lottery!
- Welcome to ‘ABC’ dating site, all the girls are waiting for you!
Well I certainly encountered few of these and as good as it seems, their all fake and these are all spam. These annoying advertising falls under spam, and according to research, about 98% of spam emails comprises of these annoying emails.
The origins of spam were analyzed by Cisco Systems in 2011 and most are being originated from United States, Brazil and followed by China.
While these emails are annoying and rather harmless, the remaining two percent are harmful which includes phishing emails to steal your personal information, financial information and user credentials.
The Nigerian princes that promise riches on behalf of a small payment done by Western Union is an example of a spam email which can steal your money.

While there are other emails which target you to click on attachments and links on the email which will load your system with malware and even fall under a phishing scam.
So what is spamming?
Spamming is any kind of unwanted, unsolicited digital communication sent to large number of recipients by the use of messaging systems (mostly email). The purposes might be for commercial advertisement, for sending false information or for any kind of fraudulent activities (like phishing).
Spam is a huge waste of time and resources. There are many applications of spam (which will be covered along the way) which is used for marketing purposes and illegal criminal purposes. In the age we live in now, the email applications come equipped with spam filters. However, users waste their time on what passes through.
According to Oracle Dyn the total cost of spam in terms of productivity, energy and technology adds up to $130 billion each year.
Bottom line is, if there is an inbox, spammers will clog it.
So spam is only in emails? No.
Spam can be found all over the internet including internet forums, text messages, blog comments, social media among many more. But email spam has made its way to the top as it is the most prevalent and often most threatening to consumers.
Spamming is an economically viable solution because advertisers have no operating costs other than managing their mailing lists, servers, infrastructures and domain names. Before we go ahead to the details of spam in your inbox today, let’s go back in time and familiarize ourselves when and how spam started.
History of Spam

- The first ever spam was sent out as a telegraphic message in 1864 which was an advertisement about a dentist.
- The earliest documented spam was an advertisement of a new computer model of Digital Equipment Corporation which was sent over the ARPANET in 1978. The backlash was instantaneous but they manage to make some sales out of it.
- Spamming was used as a prank by participants in gaming platforms to fill their rivals’ accounts with unwanted electronic junk.
- In 1994 Usenet was used as a medium to advertise about immigration law services by two lawyers (husband and wife). This was commonly known as the “green card spam”.
- In 1994 Usenet was used to send out posts in bulk, attempting to raise funds to rescue children who were at risk during the Bosnian war.
- Within a few years (by 1999) the focus of spamming moved to email where it remains today.
Spam started just as email did, as a thought experiment. While email systems were set up initially to communicate between two computers in the same room, then on the same floor, then same building, and finally on the same network.
In the early 90’s it was hard to acquire email addresses and when an email was sent it was easier to block it. So the next step by the spammers was to forge addresses and domains which was countered by blocking the IP addresses. The next measure taken by the spammers was to use domains as it was readily available, which was used mainly for spamming. This made the industry to block entire domains.
In the early 2000s, hackers developed malware which was inserted into individual computers to form vast botnets which are still dealt till this day. Also while the initial goals of spam was to make users buy actual services and goods, it took a complete shift.
Soon spam turned into illicit drugs, pornography, advance-fee fraud scams, fake dating websites, counterfeit goods and so on. Phishing also came into this world through spam. Hackers wanted to get email credentials so that a spammer could use them to send more spam (pretty straightforward).
Cyber criminals changed their attention from email credentials to financial accounts which made the phishing scams to target higher-value targets like the bank accounts of small and medium sized enterprises (SMEs).
Spam in different media

Spam can be found in a number of places;
- Email spam
- Usenet newsgroup spam
- Mobile phone messaging spam
- Social media spam
- Spam in blogs
- Spam in video sharing sites
- VoIP Spam
- Web search engine spam
- Wiki spam
- Online classified ads spam
- Internet forum spam
- Junk fax transmissions
- Spam mobile applications
- File sharing spam
We will explain some of these type of spams for you to have a better idea.
Email Spam

Email spam or commonly known as junk mail or unsolicited bulk email (UBE) is the process of sending unwanted email messages in large quantities. During the mid 90’s when email was available for the public, spam became a headache and from then it grew exponentially over the years.
If we talk numbers, by 2007 80% to 85% of all email were spam.
Since, this was a problem governments, email service providers and security firms started filtering the spam and by 2014 the numbers were reduced to 66% of all email.
Due to spam populating the inboxes of many, many people started harvesting email addresses and selling the compiled databases to spammers. A common approach relies on users not reading the finer details of agreements which results in giving consent to receive spam emails.
Newsgroup forums
Newsgroup spam is a type of spam which targets Usenet newsgroups. Spamming of Usenet newsgroups was used even before e-mail spam surfaced. Spamming is defined in this case as multiple postings of the same content (messages) over and over again.
Mobile phone spam

Mobile phone spam is the text messages you get on your phone. This is really annoying for two reasons: the phone keeps beeping with unwanted messages and in some markets, you are charged for incoming texts.
However now, there are regulations in the US where SMS messages has to have options of HELP and STOP which complies with the CAN-SPAM regulations. The STOP feature will end communications with the advertiser completely.
Spam on social media

Social Media are not immune to spam. Facebook and Twitter has spam lurking inside the platforms. The spammers will populate the feed, chat and comments with unwanted content. It is used in many ways including bulk messages, insults, malicious links, fraudulent reviews are a few among many.
With the case of Facebook, spammers will hack into accounts and send spam (like false links, messages, etc.) to their ‘friends’ by disguising himself as friends or family.
In Twitter spammers gain credibility by following verified accounts and if the owner follows back, that legitimizes the spammer. This allows the spammer to send spam as he see fits.
Spamming in blogs
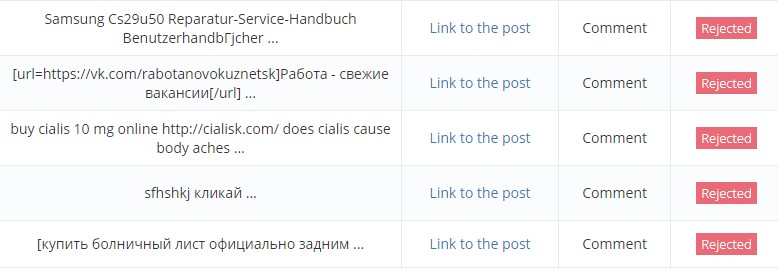
This type of spamming occur on blog sites (stating the obvious). Initially blog sites had an open nature so that people can comment freely and this led to spamming. Most of the time the spammer will repeatedly comment on the blogs with a link to his/her website.
Even in today’s day and age this tactic is still being used. But since most blog sites has approval system in place, the spam can be filtered out. The above picture shows all the spam that have been rejected.
Spam on video streaming sites

Just like spamming on blog sites, spammers can repeatedly spam on the comment section. However they will be filtered by the streaming services. While these spamming occur as text, there’s also video spam.
In video scamming the uploaded video is given a name and description with a popular figure or event that will attract attention from users. Some videos have certain timed images to come up as the videos thumbnail image to mislead viewers like a still image from a popular movie.
While some videos show a simple text or image guiding the viewers to click on the link on the description which leads to a different site. These links can lead to online surveys, different websites, or worst case installs malware.
Other video uploads will be to promote a product or service by focusing on actors and paid testimonials. These type of videos are the ones that do not qualify for the standards of a television studio.
VoIP spam

Voice over Internet Protocol is similar to telemarketing phone calls over traditional phone lines. This happens when a user chooses to opt in to receive spam calls where usually a prerecorded spam message or advertisement is played.
This is easy and cheap for spammers because calls over the internet is cheaper than traditional phone calls and it’s easy to anonymize the calls from all over the internet. The spam IP addresses and accounts can be usually identified by taking into account:
- A large number of outgoing calls
- Low call completion
- Short call length
The most common mobile phone scams are prerecorded scam messages supposedly from banks, credit card companies, and debt collectors. There are many applications of mobile phone scams.
Mobile Applications
Spamming in mobile app stores are mainly in three forms:
- Applications that were automatically generated which has no specific function or any meaningful description
- Same application published multiple times to increase the visibility in the app market
- Applications that excessively use unrelated keywords to attract users
Spam incorporated with malware
While most spam is harmless, there are some which comes hand-in-hand with different types of malware. The spammer has his own motive which results in what type of malware is sent out. Let’s briefly go through the type of unwanted programs that come with spam:
There are different types of malware that exist today. Check out the data from AV Tests total malware which shows the amount of malware over the years.
Malware are integrated with spam emails and each type of malware has a specific function.

Macro Virus
These type of viruses can run on all platforms and are usually embedded within word and excel files. When a macro virus infects a system it causes a sequence of actions to begin automatically when the infected applications are opened.
Stealth virus
This has the power to hide modifications by intercepting antivirus calls to the operating system and provides false information.
Polymorphic virus
This virus makes identical copies of itself on your system. This will take a lot of your CPU power which will affect the performance.
Self-garbling virus
These type of viruses hide from antivirus software by modifying its code.
Key loggers
Key logging is the action of recording the keys struck on a keyboard, without the victim having any knowledge of the issue. The data can be retrieved by the person operating the logging program.
Trojan horse
This is a type of malware often disguised as a legitimate software. These are used by spammers and cyber criminals to retrieve user data.
Bots and Zombies
A bot or zombie is a computer that a remote attacker has accessed and set up to forward transmissions (including spam and viruses) to other computers on the Internet. The purpose is usually either financial gain or malice.
Types of Spam
There are different types of spam out there with different intentions. On one side of the spectrum we have the annoying marketing spam while the other end has the serious threats. These include cybercriminals attempting to break into online accounts, steal data and spread malware.
Marketing spam is annoying but it’s not a threat. These are usually filtered out by your email providers and what passes through the cracks can easily be identified. The others are not so easy.
- Advance-fee scam
- Phishing scam
- Malspam
- Steganography
- Spam on mobile
- Drive-by-attacks
- PuPs
Advance-fee scams

Advance-fee scams or the Nigerian scam or 419 scam involves a mysterious sender which offers a huge reward in exchange for a small payment. Usually a small processing fee to unlock the grand prize. Once the cash is wired to the cybercriminal, he disappears with the money.
Note that the name ‘Nigerian scam’ was put in place as the advance-fee scams were originated from Nigeria. However these type of scams are being done all over the world and only a small fraction is from Nigeria itself.
Another variant of the advance-fee scam is turning victims into money mules. These are described by scammers as ‘payroll management jobs’ where the victim’s bank account is used to launder and transfer money. In exchange, the victims get to keep a fraction of the money.
Even though these seem easy to avoid, often people fall for them each day due to the tricks used by the scammers. These tricks are social engineering tactics which manipulates a victim by using psychology.
Phishing emails

Phishing is a cybercrime which makes use of social engineering techniques in order to steal user data like login credentials and financial details. The most common type of phishing attacks take place through emails. An attacker sends an email pretending to be from a trusted source tricking the victim into opening the email and clicking on the attached link (or download attachments).
Once the malicious link is clicked, one or more of these things will happen:
- Redirects to a fake website which requests personal information (login credentials, credit card details etc)
- Installs malware on your system
- Leads to a ransomware attack by freezing your device
- Revealing of sensitive information
- Installation of software with the intent of stealing information (Keyloggers)
The motive is “why pick a lock when you can get the key from the owner”.
Malspam

Any kind of malware spread out through spam falls under the category; malspam. Just like advance-fee and phishing scams, this also relies on social engineering techniques. They will trick a recipient to take actions like downloading attachments, clicking on links or even opening attachments which infects the user’s device.
The downloadable attachments are usually in the format of PDF, PowerPoint and Word files with malicious codes (like macros). When attachments are opened, the scripts run and malware are retrieved from the servers of cybercriminals.
As mentioned above, the malware can infect your system to be part of a botnet or can also be a Trojan. The majority of malware attacks occur usually with the use of Trojans.
Steganography
While spam has a negative image, one of the ‘good’ applications of spam is the use of steganography. This is the practice of concealing messages or information within other non-secret text. Usually this is to send important information between people.
However this is not encryption but it’s a way to secretly hide a message within the texts of spam emails. There’s a cool site where you can encode and decode spam, check it out.
Here’s an example:
I wanted to encode the phrase “transfer me bitcoin” and pressed encode.

After pressing encode, I got a spam email which has the message hidden inside.
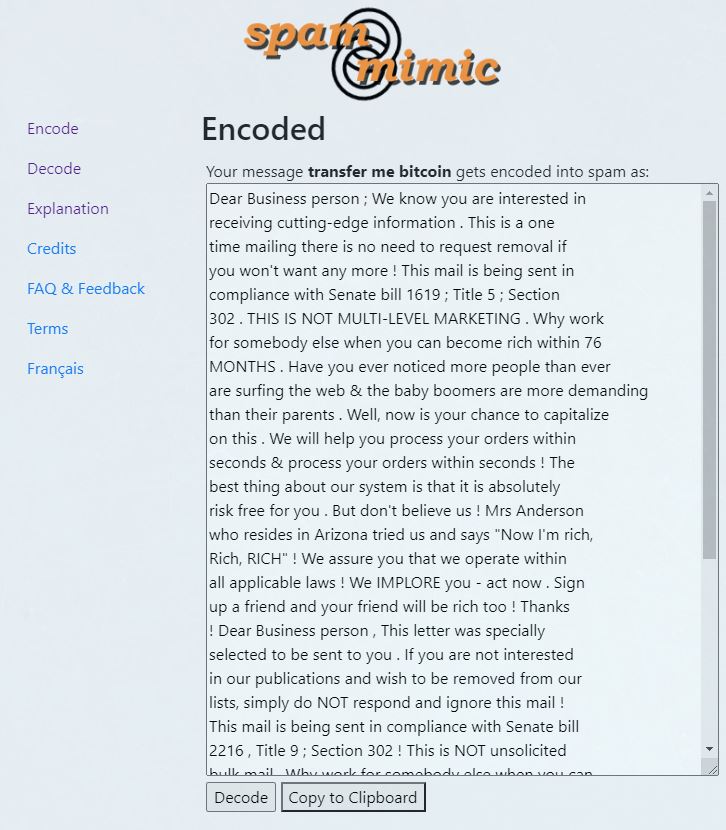
To check if it works, simple copy the text and go to decode and you will get the hidden message.
Conclusions
As you saw till now, spam has been around quite a long time and it won’t be coming to an end anytime soon. There are a few things you can do to avoid spam:
- Don’t respond to spam
- Turn your spam filter on
- Turn off macros
- Be vigilant about phishing emails (check our article)
- Use two factor authentication
- Install cybersecurity software
Let us know what you think in the comments below. Happy and safe surfing!
Do you value your privacy online?
Use VPN Surf and surf safely and securely in the open waters of the internet.
