
WIFI security algorithms have been around since the 1990s which has gone through many changes and upgrades throughout the years. Different types of wireless security protocols came into being from the 1990’s till now. They are:
- WEP (Wired Equivalent Privacy protocol)
- WPA (WIFI Protected Access protocol)
- WPA2 (WIFI protected Access 2 protocol)
They all serve the same purpose but in different levels. These protocols help keep unwanted parties from connecting to the network and also encrypts the data travelling to and from the WIFI routers.
To put it into perspective imagine that your PC is connected to the router via an Ethernet cable. This enables the data packets to get from point A to B through the wire. With WIFI the data packets are broadcasted to all directions and can be received by all connected devices.
Without the security protocols in place, your data can be intercepted by anyone and we don’t want that now do we. So let’s get familiar with the security protocols:

WEP – Wired Equivalent Privacy
WEP is the most widely-used WIFI security protocol in the world and the first security protocol to be introduced to the world in 1999. This protocol appears first in the protocol selection menus in many router control panels.
Initially these were not as strong as they used 64-bit encryption, but then it changed into 128-bit encryption and remain to be one of the most common implementations. Even though the protocol had an increased key size, with time other security flaws started to surface.
As the power of computers started increasing it became easier to exploit those flaws and by 2004 the WIFI Alliance officially retired WEP. There were many people who tried to improve it and bring back the protocol but it remained highly vulnerable.
If your system relies on WEP, then you should upgrade to a different protocol immediately. IF there are no options, then it’s better to replace the WIFI router.
WPA – WIFI Protected Access
WPA was the successor of WEP which countered the prevailing vulnerabilities. This was adopted in 2003, a year before WEP was officially retired.
The most common configuration is WPA-PSK (Pre shared key) where a key is shared before a session between the parties to have higher security. The keys being used are 256-bit and this is a big upgrade from the 128-bit encryption used in WEP systems.

The most significant changes were the message integrity checker and the Temporal Key Integrity Protocol (TKIP). The message integrity checker determines if an attacker has captured or altered the data packets passing between the access point and client. TKIP uses a per-packet key system which was more secure than the fixed key system used in WEP systems.
Despite what a significant improvement WPA was over WEP, the ghost of WEP haunted WPA. TKIP, a core component of WPA, was designed to be easily rolled out via firmware upgrades onto existing WEP-enabled devices. As such, it had to recycle certain elements used in the WEP system which, ultimately, were also exploited.
There are also flaws with WPA however, usually it’s not breached by directly attacking the WPA protocol but by attacks on the WIFI Protected Setup (WPS) which was made to easily link devices.
WPA2 – WIFI Protected Access
WPA2 is the successor of WPA and the most significant change between the two is the mandatory use of AES algorithm and CCMP (Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) as a replacement for TKIP.
However TKIP is still preserved with WPA2 as a fallback system.
This is the protocol that we use at this day and age which is stronger than all the previously introduced protocols. This doesn’t mean its fool proof. The main vulnerability is if an attacker gets access to the secured network, they can access certain keys and then perpetuate an attack against other devices on the network.
However to note that the security implications of the known WPA2 vulnerabilities are limited almost entirely to enterprise level networks and deserve little to no practical consideration in regard to home network security.
Unfortunately the WPS vulnerability still remains but it takes 2 to 14 hours of sustained effort with a modern computer to crack it. We shouldn’t consider this lightly as it is still a flaw in the system.
We recommend to disable WPS and, if possible, the firmware of the access point should be flashed to a distribution that doesn’t even support WPS so the attack vector is entirely removed.
How to find the security protocol from Windows 10?
Now we know about the security protocols. Time to test it out and check it ourselves.
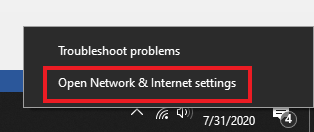
- Right click on WIFI icon on the taskbar (bottom right corner)
![]()
- Click on “Open Network & Internet settings”
- Click on properties under the connected WIFI

- Under the data you will see a lot of data including the security protocol being used. Check besides ‘Security type’

Which WIFI security protocol is better?
By now you have an idea of the security protocols being used in your WIFI. We recommend to use the latest and most secure security version WPA2 protocol. However sometimes depending on the usage the other protocols might be better. If it’s for home usage we recommend using the WPA2 protocol.
You can select the protocols once you login to your router. It will look something like the picture below.
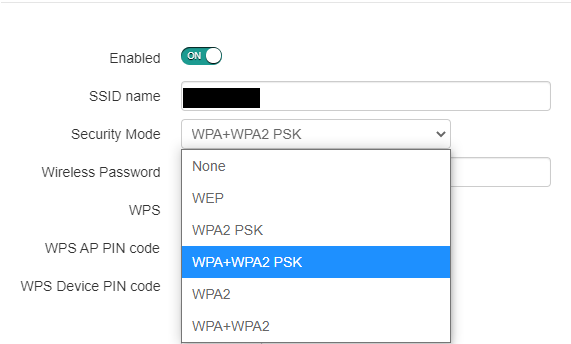
IF you would like to learn more about protecting your WIFI at home give this article a read.
Congrats! You made it till the end. Let us know what you think in the comments below.
Do you value your privacy online?
Use VPN Surf and surf safely and securely in the open waters of the internet.
