
Technology has definitely performed a giant leap over the last few decades. We went from button phones that had two functions: call and text, (the former being a real chore to do) to having small computers in our pockets that can perform nearly any task that a full desktop can.
These smartphones contain nearly all personal information about us since they hold our messages, pictures, bank account details, and much more.
Fortunately, there are security measures in place that keep others from accessing this sensitive information.
Originally this was done by using passwords and pin codes but having to enter either of the aforementioned methods every time someone wants to unlock the phone is simply inconvenient for most users. That is why smartphone manufacturers started to explore different, faster ways one could unlock their devices.
So, biometric security on smartphones was born.
What are biometrics?

Put simply, biometrics are any metrics related to human features.
They measure a person’s physical characteristics to verify their identity. Any time you are using your fingerprint or facial recognition to unlock your smartphone or laptop, you are using biometrics.
Undeniably there are many advantages to using biometric security on your devices. A pin lock or a password can be cracked, while to fool a fingerprint scanner, someone would actually need to physically recreate your fingerprint, which is possible but very hard to do.
Biometric authentication methods are also much faster that entering even a simple four number pin.
Unfortunately, whenever there are advantages, there are also downsides. Although biometrics originally got popular from using fingerprints and iris scanners, there is a new method that certain smartphone and laptop manufacturers are pushing. It is facial recognition.
Despite being as secure as the previous methods, this biometric authentication approach carries a much more dangerous context.
What is facial recognition?

Facial recognition is a way for technology to recognize a human face. It does so in a similar fashion of another human being recognizing a face. People are good at recognizing familiar facial features:
- the eyes
- nose
- mouth
- chin and how they all come together to form a face.
That’s basically how a facial recognition system works but on a much larger and algorithmic scale. There are a few different methods of how a facial recognition system works, but in general, they extract selected facial features from an image or video and compare this data to the information that is stored in the database.
The history of facial recognition technology
Now that we know what facial recognition is, let’s delve into its history for a bit to get a better idea of how it works and understand the initial reasons why it was invented.
Despite appearing on consumer products only in the late 2010s, the technology itself has been around for more than half a century.
First developed in 1965 with a quite high error rate, most the work on the original algorithm could not be published as it was funded by an unnamed intelligence agency (yes, even to this day).

Based on the best available references, this approach used manual marking (using a graphics tablet) of different landmarks on the face such as the center and corners of the eye, nose, mouth, etc. To determine the identity, the distance between these landmarks was computed and compared to other images.
The method allowed the processing of around 40 images per hour!
How does facial recognition work?
Although when broken down to the basics, all facial recognition techniques use data from a face in an image to compare it to the data already contained in the database, there are different techniques in which this data can be obtained.
Each one has its own ups and downs, and might require different hardware and software to execute.
There are five main methods of extracting data from a picture of a human face.
They are as follows:
1. Traditional Facial Recognition
As can be inferred from the name, this method uses a similar algorithm to that which was used back in the 1970s when the technology was just being developed. The facial recognition algorithm identifies different facial features through extracting landmarks from an image of a face.
It then compares the shapes of different facial structures such as the eye and nose shape and their relative position between one another. These images are then compared to other images in the database with matching features.
Although originally the landmarks on the face were marked manually, nowadays, the computer recognizes these features on its own.
There are two main classifications of traditional facial recognition:
- Holistic: attempts to recognize the entire face
- Feature-based: divides the face into the landmarks and compares their shape and spatial location with respect to each other.
2. 3 – Dimensional Recognition
Unfortunately, when referring to device security, traditional facial recognition can be fooled quite easily. All that is needed is a clear picture of your face and your device is unlocked.
This is where 3-dimensional facial recognition comes into play. Three-dimensional face recognition technique uses 3D sensors to capture information about the shape of a face.
This information is then used to identify distinctive features on the surface of a face, such as the contour of the eye sockets, nose, and chin.

When used in device security, another advantage 3D face recognition has over the traditional method is that it is not affected by changes in lighting like other techniques. It can also identify a face from a range of viewing angles, including a profile view.
Three-dimensional data points from a face vastly improve the precision of face recognition.
3D research is enhanced by the development of sophisticated sensors that do a better job of capturing 3D face imagery.
3. Skin Texture Analysis
Being a more recent development, this method of facial recognition is not fully developed to work 100% of the time on its own. Instead, it is usually combined with either of the aforementioned methods to improve their accuracy.
Skin texture analysis uses the visual details of the skin, as captured in standard digital or scanned images. This technique turns the unique lines, patterns, and spots apparent in a person's skin into a mathematical space.
Surface Texture Analysis works much the same way facial recognition does.
A picture is taken of a patch to distinguish any lines, pores, and the actual skin texture. It can identify the contrast between identical pairs, which are not yet possible using facial recognition software alone.
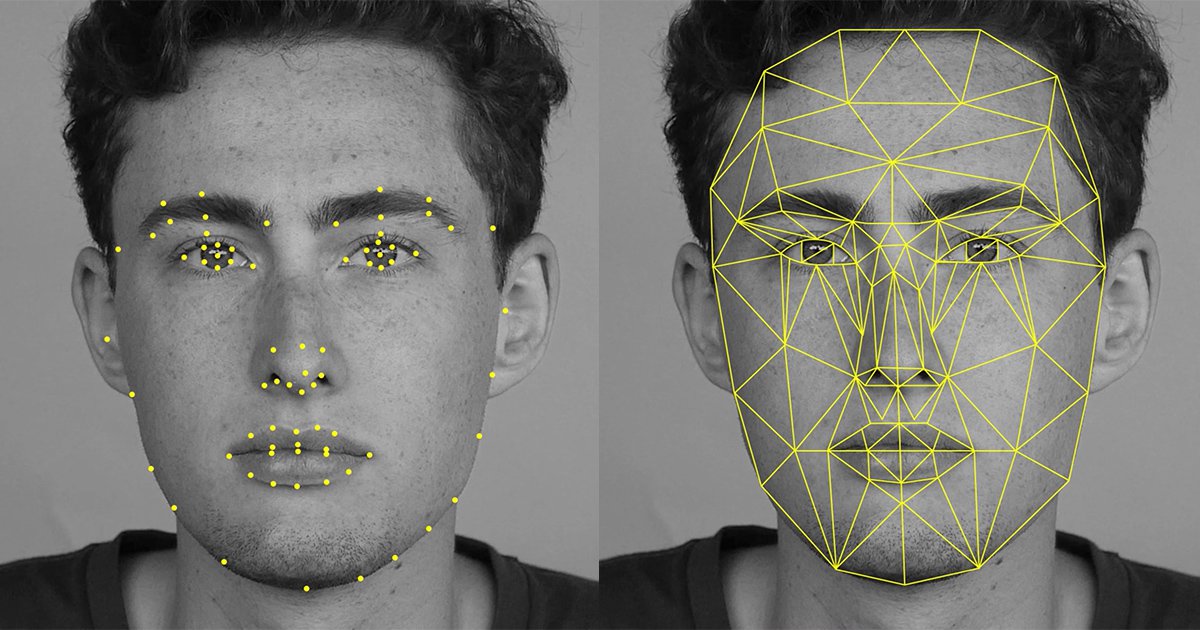
4. Facial Recognition Combining Different Techniques
As every method has its advantages and disadvantages, technology companies have amalgamated the traditional, 3D recognition and Skin Textual Analysis, to create recognition systems that have higher rates of success.
Combined techniques have an advantage over other systems. It is relatively insensitive to changes in expression, including blinking, frowning or smiling and has the ability to compensate for mustache or beard growth and the appearance of eyeglasses.
The system is also uniform with respect to race and gender.
5. Thermal Cameras
A different form of taking input data for face recognition is by using thermal cameras, by this procedure the cameras will only detect the shape of the head and it will ignore the subject accessories such as glasses, hats, or makeup.
Unlike conventional cameras, thermal cameras can capture facial imagery even in low-light and nighttime conditions without using a flash and exposing the position of the camera.
However, a problem with using thermal pictures for face recognition is that the databases for face recognition are limited.

Facial Recognition Applications
We have already discussed the use of facial recognition for the purposes of device security; however, facial recognition has many other applications as well.
Many published works mention numerous applications in which face recognition technology is already utilized including entry to secured high‐risk spaces such as border crossings as well as access to restricted resources.
On the other hand, there are other application areas in which face recognition has not yet been used. The potential application areas of face recognition technology can be outlined as follows:
- Automated surveillance, where the objective is to recognize and track people.
- Monitoring closed-circuit television (CCTV), the facial recognition capability can be embedded into existing CCTV networks, to look for lost children or other missing persons or tracking known suspected criminals.
- Image database investigations, searching image databases of licensed drivers, benefit recipients, and finding people in large news photograph and video collections, as well as searching in the Facebook social networking web site.
- Multimedia environments with adaptive human-computer interfaces (part of ubiquitous or context-aware systems, behavior monitoring at childcare or centers for old people, recognizing customers and assessing their needs).
- Airplane‐boarding gate. The face recognition may be used in places of random checks merely to screen passengers for further investigation. Similarly, in casinos, where strategic design of betting floors that incorporates cameras at face height with good lighting could be used not only to scan faces for identification purposes but possibly to afford the capture of images to build a comprehensive gallery for future watch‐list, identification and authentication tasks.
- Sketch‐based face reconstruction, where law enforcement agencies in the world rely on practical methods to help crime witnesses reconstruct likenesses of faces. These methods range from sketch artistry to proprietary computerized composite systems.

- Forensic applications, where a forensic artist is often used to work with the eyewitness in order to draw a sketch that depicts the facial appearance of the culprit according to his/her verbal description. This forensic sketch is used later for matching large facial image databases to identify the criminals. Yet, there is no existing face recognition system that can be used for identification or verification in crime investigation such as a comparison of images taken by CCTV with available databases of mugshots. Thus, utilizing face recognition technology in forensic applications is a must.
- Face spoofing and anti‐spoofing, where a photograph or video of an authorized person's face could be used to gain access to facilities or services. Hence, the spoofing attack consists of the use of forged biometric traits to gain illegitimate access to secured resources protected by a biometric authentication system. It is a direct attack on the sensory input of a biometric system, and the attacker does not need previous knowledge about the recognition algorithm. Research on face spoof detection has recently attracted increasing attention, introducing few numbers of face spoof detection techniques. Thus, developing a mature anti‐spoofing algorithm is still in its infancy and further research is needed for face spoofing applications.
There have been envisaged many applications for face recognition, but most commercial ones exploit only superficially the great potential of this technology. Most of the applications are notable limited in their ability to handle pose, lighting changes or aging.
In reference to access control, face verification during face‐based PC login has become feasible but seems to be very limited. Naturally, such PC verification system can be extended in the future for authentic single sign‐on to multiple networked services or transaction authorization or even for access to encrypted files.
For example, the banking sector is rather conservative in deploying such a biometrics system. They estimated high risk in losing customers disaffected by being falsely rejected than they might gain in fraud prevention. It is the reason for robust passive acquisition systems development with low false rejection.

Most physical access control systems use face recognition combined with other biometrics, such as iris scanning or fingerprint authentication.
One of the most interesting factors in face recognition in the application domain associated with surveillance. Regarding the dangerous type of information it contains, video is the medium of choice for surveillance. For applications that require identification, face recognition is the best biometric for video data.
The biggest advantage of this approach is the passive participation of the subject (a human). The whole process of recognition and identification can be carried out without the person's knowledge.
Although the development of face recognition surveillance systems has already begun, the technology seems to be not so accurate. It also brings additional problems concerning highly extensive perception in the data gathering and computing side of such complex solutions.
The Dangers Behind Facial Recognition
Although as can be seen previously, facial recognition can and is used as a very beneficial technology, there are also some things that you need to be aware of with the implementation of it. Here are some malicious things that can be done with the help of facial recognition:
1. Identity Fraud
If facial data gets compromised, it poses huge threats to governments as well as ordinary citizens. If the security measures employed with facial recognition technology are not stringent enough, hackers can easily spoof other peoples’ identities to carry out illegal activities.
This may result in huge financial losses if the data required for financial transactions gets stolen or duplicated. Financial institutes employing facial recognition methods for providing financial services must ensure to provide strict security measures to protect user data.
In the consumer electronics space, mobile companies employing facial recognition technologies in mobile devices aren’t foolproof. Apart from a few manufacturers, most facial recognition tools are nothing more than gimmicks.
These systems can be fooled easily leading to compromise of user data. However, the instances of identity fraud are decreasing due to increasingly advanced security measures. Fooling a facial recognition system has become difficult, but it’s still not impossible.

2. Data Theft
Facial recognition software depends on and generates a large amount of data. Storage of data becomes a major concern with this technology. However, the prevention of data theft is a bigger concern regarding technology.
Database hacking can compromise the data of thousands, if not millions of people. There have been numerous instances of data theft from publicly accessible databases. Prevention of data theft should be one of the priorities while implementing facial recognition technologies.
Once the user data is compromised, its compromised forever. This poses a significant threat as the data can be misused for a long period of time if the issue is not resolved.
Agreed, there are various dangers of facial recognition technology. However, these risks can be limited by the use of proper implementation of technology.
Safe storage of facial recognition data and ethical use will help eliminate the major concerns regarding the use of facial recognition technology. A healthy debate regarding the implementation of facial recognition technology by governments as well as private institutes is the need of the hour to find a suitable solution to the issues faced by the technology.
3. Unethical Use
One of the significant dangers of facial recognition is the unethical use of technology. Gathering facial data without consent is one thing. However, collecting information without the user even being aware raises a huge debate regarding the unethical use of the technology.
Hidden cameras are being employed at various places without the user being aware. Such data can be exploited and can be used unethically, compromising the data of unaware citizens.
This not only violates an individual’s right to privacy but also infringes his right to information. For example, a pizza restaurant in Norway was found to be using facial recognition technology with hidden cameras for delivering gendered advertising.
Such instances can greatly harm the reputation of the firms carrying out such illegal activities.
Organizations must abstain from putting such practices in place which gather data without the knowledge of the concerned people. Facial recognition technology can be deployed selectively too. For example, it can be used to identify illegal citizens and refugees or racial profiling. Deployment of controversial facial recognition technology poses concerns regarding human rights. Thus, human rights should be of prime importance while implementing facial recognition technology.
Do you value your privacy online?
Use VPN Surf and surf safely and securely in the open waters of the internet.
